Quantum Cryptography in Secure IoT Communications
A new age in cybersecurity is being heralded by the convergence of Quantum Computing with the Internet of Things (IoT), offering previously unheard-of levels of encryption and data protection. The proliferation of IoT devices in various businesses and daily life underscores the critical need to ensure their security. It is difficult for traditional cryptographic techniques to keep pace with the growing volume and complexity of Internet of Things networks. But the emergence of Quantum IoT offers revolutionary solutions that improve cryptographic algorithms and secure communications by utilising the ideas of quantum physics.
We explore the exciting field of quantum IoT in cryptography and secure communications in this essay. We examine how quantum technologies, which provide strong defence against new attacks and vulnerabilities, are changing the cybersecurity landscape for Internet of Things devices. We explore the potential effects and long-term ramifications of incorporating quantum concepts into IoT security protocols, ranging from quantum key distribution to quantum-resistant encryption.
Understanding Quantum Technology in IoT
When we talk about Internet of Things (IoT) systems, we’re referring to the use of quantum technologies and principles to enhance their security and functionality. It covers topics such as quantum sensing, quantum cryptography, quantum computing, and quantum communication. While quantum communication ensures secure, impenetrable data transfer between IoT devices, quantum computing enables faster data processing and more sophisticated analytics. For industrial control and environmental monitoring, quantum sensors give increased sensitivity and precision. Meanwhile, quantum cryptography offers sophisticated encryption techniques to safeguard Internet of Things data against cyberattacks.
Take an Internet of Things network for smart cities that leverages quantum technology. By analysing real-time data from traffic sensors and making more accurate predictions about traffic patterns, quantum computing can improve traffic flow. Secure communication between connected cars and traffic management systems is ensured using quantum communication, which guards against illegal access and traffic signal manipulation. More accurate air quality monitoring is possible thanks to quantum sensors, which enable data-driven decision-making for municipal planners to control pollution. Furthermore, within the Internet of Things infrastructure, quantum cryptography guarantees the confidentiality and protection of sensitive data, including emergency response data. Efficiency, security, and sustainability are all improved in urban settings when quantum technology is included in innovative city Internet of Things systems.
How does it intersect with IoT?
The Internet of Things (IoT) is one of the many businesses that could transform thanks to the rapidly developing field of quantum technology.
This is a summary of how IoT and quantum technology interact:
Enhanced Security: The sophisticated cryptographic methods enabled by quantum technology can significantly improve the security of Internet of Things networks and devices. For IoT applications, quantum encryption techniques such as quantum key distribution (QKD) provide secure channels of communication that are impenetrable to hackers. This guarantees data confidentiality and integrity.
Faster Data Processing: Handling the enormous volumes of data generated by IoT devices requires speedier processing and analysis, which quantum computing enables. Compared to classical computers, quantum computers are far more efficient at performing complex computations and simulations, thereby improving real-time analytics and decision-making in Internet of Things systems.
Improved Sensor Technology: Compared to conventional sensors, quantum-based accelerometers, gyroscopes, and magnetic field sensors have superior sensitivity and precision. By integrating these quantum-enhanced sensors into IoT devices, more precise industrial control, navigation, and environmental monitoring applications are made possible.
Optimised Network Efficiency: In Internet of Things installations, quantum technology also helps to optimise network efficiency. For Internet of Things devices spanning large geographic areas, quantum communication protocols provide secure, high-speed data transmission over long distances, reducing latency and improving overall network performance.
Energy Efficiency: Algorithms and optimisation strategies inspired by quantum principles can help make Internet of Things systems more energy-efficient. IoT applications can achieve greater resource utilisation, lower energy consumption, and longer battery life for connected devices by utilising quantum concepts in algorithm design.
Future Potential: As quantum technology continues to develop, its integration with IoT is anticipated to reveal new features and applications. This includes quantum-secure communication protocols for vital IoT infrastructure, quantum-enhanced sensor networks for environmental monitoring, and quantum-enabled machine learning algorithms for predictive analytics.
To overcome technological obstacles, ensure interoperability, and establish robust security standards, researchers, business leaders, and legislators must work together to fully understand and leverage the promise of quantum technology in the Internet of Things. These technologies have the potential to revolutionise IoT ecosystems and open up new avenues for innovation in a variety of industries as they merge.
Key Aspects
The term “quantum technology” in Internet of Things (IoT) refers to the incorporation of quantum concepts, tools, and methods into IoT applications and systems. It entails utilising developments in quantum sensing, quantum computing, quantum communication, and quantum cryptography to improve the functionality and efficiency of Internet of Things networks and devices. Here are a few crucial IoT applications for quantum technology:
Quantum computing
Quantum computing is the application of quantum-mechanical phenomena, like entanglement and superposition, to computation. Quantum computing can enable faster data processing, more sophisticated analytics, and optimisation algorithms that improve the effectiveness and performance of Internet of Things systems. Quantum computers are useful for Internet of Things applications that require high-performance computing because they can manage enormous datasets and tackle computational challenges beyond the scope of classical computers.
Quantum Communication
IoT devices can have secure, unhackable communication channels thanks to quantum communication technologies such as quantum key distribution (QKD) and quantum teleportation. To securely exchange encryption keys and ensure that data sent between Internet of Things devices remains private and protected from cyberattacks, QKD leverages quantum principles. Low-latency long-distance data transfer is another benefit of quantum communication for Internet of Things installations in dispersed networks.
Quantum sensing
To measure physical quantities with greater sensitivity, accuracy, and resolution, quantum sensors exploit quantum phenomena, such as atomic spin states and quantum interference. These sensors can be included in Internet of Things devices for use in industrial control systems, medical diagnostics, and environmental monitoring, among other applications. With benefits such as lower noise, a higher signal-to-noise ratio, and increased precision, quantum-enhanced sensors make data gathering and analysis in Internet of Things contexts more reliable.
Quantum cryptography
By leveraging quantum properties to enable unbreakable encryption, quantum cryptography approaches offer advanced security mechanisms for Internet of Things networks. IoT data is protected from prying eyes and unauthorised access through quantum key distribution (QKD) protocols such as BB84 and E91, which generate and distribute cryptographic keys securely using quantum principles. Quantum cryptography addresses cybersecurity issues in linked devices and systems by guaranteeing the integrity, secrecy, and authenticity of communications in Internet of Things deployments.
Organisations across industries, including smart cities, healthcare, transportation, and manufacturing, can open new avenues for innovation, data-driven insights, and secure communications by incorporating quantum technology into IoT systems. It’s crucial to remember that quantum technology is still in its infancy and that, to overcome technical difficulties and scalability concerns, widespread use in Internet of Things applications may require additional research, development, and standardisation initiatives.
Challenges in Traditional Cryptography
In the current digital environment, traditional cryptography faces several challenges, particularly as technology advances and cyber threats become more complex. The following are some significant obstacles:
Key Management
Managing keys is one of the main issues with classical cryptography. Encryption and decryption in cryptographic systems depend on keys; therefore, creating, distributing, and securely storing keys becomes essential. As the number of communication parties increases, key management becomes more complex, increasing the risk of vulnerabilities if keys are lost, stolen, or mishandled.
Algorithm Vulnerabilities
As processing power and algorithmic advances increase, classic cryptographic algorithms such as RSA and AES are increasingly vulnerable to attacks. Data security can be compromised by cryptanalytic techniques such as side-channel attacks, differential cryptanalysis, and brute-force attacks, which exploit flaws in algorithms or implementations.
Quantum Computing Threat
The development of quantum computing presents a danger to established cryptography. Widely used encryption techniques like RSA and ECC could be broken by quantum computers using efficient factoring algorithms such as Shor’s algorithm. The creation and implementation of cryptographic protocols and algorithms that are resistant to quantum technology is crucial.
Key Exchange over Unsecured Channels
It might be difficult to securely exchange cryptographic keys over unprotected channels, such as the Internet. Strong key exchange protocols, such as the Diffie-Hellman key exchange, are essential because they can prevent man-in-the-middle attacks, in which an attacker intercepts and modifies key exchange messages, jeopardising the confidentiality and integrity of communication channels.
Scalability and Performance
Especially in large-scale systems or real-time applications, cryptographic procedures can add overhead in terms of computational resources and delays. It is crucial to strike a balance between security needs and performance considerations to ensure effective, scalable cryptographic systems without sacrificing data security.
Research and development in cryptographic protocols, algorithms, key management techniques, and security best practices are necessary to meet these problems. Furthermore, implementing secure communication protocols and moving towards cryptography that is resistant to quantum attacks can reduce risks and strengthen the resilience of cryptographic systems against changing cyber threats.
Securing the Internet of Things: Quantum IoT and the Future of Encryption
The emergence of Quantum IoT marks a paradigm shift in how IoT networks and devices are secured. In contrast to conventional encryption, which relies on mathematical techniques, Quantum IoT maximises security by leveraging quantum principles such as superposition and entanglement. By utilising the properties of quantum particles, quantum encryption techniques such as quantum key distribution (QKD) enable the secure exchange of keys between Internet of Things devices. This indicates that while conventional encryption techniques like RSA and ECC may become outdated as strong quantum computers develop, quantum-resistant Internet of Things (QoT) can withstand such attacks.
Quantum IoT also has advantages over encryption. The integrity of Internet of Things data collection and monitoring can be strengthened by quantum sensors, which leverage quantum processes for greater sensitivity and precision. Data transfer is safe and effective with quantum communication protocols, which reduce the possibility of interception or tampering. These developments not only improve security but also open the door to more reliable and practical IoT applications across industries, including smart cities, healthcare, and industrial automation.
Looking ahead, Quantum IoT’s capacity to handle the changing threat landscape will determine how encryption plays out in the Internet of Things. Quantum IoT is an essential defence mechanism that will help the connected world of IoT remain safe, reliable, and resilient against new cyber threats as quantum computing advances.
Quantum IoT: Redefining Security in the Digital Age
In cybersecurity, quantum IoT is undoubtedly revolutionary, especially in sectors such as manufacturing, automotive, and healthcare, where connected devices are widely used. Quantum Internet of Things (QIoT) offers unmatched capabilities for precise control, real-time monitoring, and sophisticated data analysis by leveraging the power of smart devices and networks. This results in increased operational effectiveness, reduced downtime from preventive maintenance, and customised customer experiences.
Quantum IoT, for example, can be used in manufacturing to optimise production processes by tracking equipment health in real time and anticipating maintenance needs before failures occur. This reduces downtime and maximises resource utilisation.
In addition to these advantages, quantum IoT also poses serious security risks. Cybercriminals can exploit the large attack surface created by the networked nature of IoT devices. Sensitive data may be vulnerable to malicious attacks, data breaches, and unauthorised access due to security weaknesses in IoT devices, weak authentication procedures, and inadequate encryption. Therefore, it is crucial to have strong cybersecurity measures in Quantum IoT implementations. These methods include access control, secure key management, end-to-end encryption, and continual monitoring for anomalies or suspicious activity.
One viable answer to these problems is the incorporation of quantum cryptography into quantum IoT systems. Quantum IoT systems are resistant to emerging cyber threats, including those posed by quantum computers, thanks to quantum-resistant cryptographic algorithms, quantum key distribution (QKD) protocols, and quantum-enhanced authentication procedures that enhance data security and integrity. The amalgamation of Quantum IoT and sophisticated cybersecurity protocols not only reshapes security norms in the digital era but also empowers sectors to confidently and securely harness the full potential of IoT technologies.
Quantum IoT in Cryptography and Secure Communications
A revolutionary development in secure communications in the digital sphere is the combination of quantum IoT with cryptography. The application of quantum computing to the Internet of Things (QoT) greatly improves encryption and data protection by leveraging concepts such as superposition and entanglement. This convergence enables the creation of cryptographic algorithms and protocols resistant to quantum adversaries, thereby guaranteeing strong security measures.
Furthermore, secure communication routes between IoT devices, networks, and platforms are made possible by quantum IoT in cryptography. Quantum encryption techniques, including quantum key distribution (QKD), make secure key exchange procedures easier to manage. They also guard against unwanted access and guarantee the integrity and confidentiality of data transferred between linked Internet of Things systems. This degree of security is essential for preventing cyberattacks, protecting private data, and preserving public confidence in IoT installations in a variety of industries.
Beyond conventional encryption methods, quantum cryptography in IoT offers prospects for improving secure communications. Digital signatures, access control protocols, and quantum-enhanced authentication techniques fortify an organisation’s overall cybersecurity posture and help create safe, reliable environments for data sharing, remote access, and IoT device management.
Quantum IoT is set to revolutionise secure communications and cryptography as it advances, fostering trust, resilience, and innovation across networked digital infrastructures and IoT ecosystems.
Quantum Key Distribution
Given the potential threat quantum computing poses to traditional secret-key systems, quantum key distribution (QKD) is essential for maintaining communication security. Quantum-based keys are required for secure Internet of Things communication, as quantum computers frequently compromise asymmetric key schemes. These quantum keys establish a secure channel between communicating entities by leveraging concepts from quantum mechanics. Secure quantum key distribution techniques include those found in BB84, BBM92, SARG04, and E91, among others. The goal of QKD is key distribution and transmission via both quantum and conventional channels. To minimise the amount of information extracted from the quantum system in accordance with the principles of quantum physics, the key distribution approach involves sharing random bits on a random basis.
Quantum Authentication
The security of messages depends on quantum authentication to verify message confidentiality and integrity. Verification of messages, integrity, and non-repudiation are guaranteed via mutual authentication between entities. Quantum Signature and Entanglement are two techniques used in quantum-based identity identification. A special characteristic of quantum communication is quantum entanglement, in which entangled particles have interdependent states that are represented as Bell states. To provide non-repudiation and defend against user impersonation attacks, quantum signature protocols, such as quantum group signature, quantum blind signature, and arbitrated quantum signature, are used to verify the identities of authenticated users.
Quantum IoT Enhancements in Cryptography
Significant improvements in cryptography are enabled by quantum IoT, primarily by resolving flaws in conventional encryption techniques. In the context of the Internet of Things (IoT), quantum IoT provides the following significant advances in cryptography:
Quantum Key Distribution (QKD)
To safely transfer encryption keys between IoT devices, quantum IoT uses QKD, a quantum cryptography protocol. QKD uses quantum features such as entanglement and the uncertainty principle to ensure that any attempt to eavesdrop or interfere with the key exchange is immediately detectable, unlike traditional key exchange systems, which are susceptible to interception. By doing this, sensitive data is shielded from unwanted access, and the security and integrity of communications in IoT networks are improved.
Post-Quantum Cryptography
As quantum computers advance, classical cryptography techniques such as RSA and ECC become vulnerable to quantum attacks. Post-quantum cryptography (PQC), which uses quantum-resistant algorithms to defend against attacks from quantum computers, is being enabled by quantum IoT. PQC algorithms offer a long-term solution for protecting IoT data against quantum attacks. Examples of these algorithms are hash-based cryptography, lattice-based cryptography, and code-based encryption.
Quantum Random Number Generation
To produce genuinely random numbers with high entropy, quantum IoT uses quantum random number generators (QRNGs). Conventional pseudo-random number generators (PRNGs) are susceptible to cryptographic attacks and can be predictable. By strengthening cryptographic protocols and key-generation procedures in Internet of Things devices, QRNGs generate naturally unpredictable random numbers based on quantum phenomena such as photon detection or quantum tunnelling.
Quantum-resistant protocols
The Internet of Things (IoT) encourages the development and deployment of quantum-resistant protocols for a range of cryptographic functions, including digital signatures, authentication, and encryption. By utilising strong security mechanisms, quantum-safe key management procedures, and quantum-resistant algorithms, these protocols are made to withstand quantum attacks. IoT devices can protect privacy and security from quantum threats by incorporating quantum-resistant protocols.
Multi-layered Security
Quantum IoT emphasises a multi-layered cryptography approach to security for IoT deployments. This entails implementing secure communication protocols, imposing access controls, integrating quantum encryption with conventional cryptographic methods, and regularly updating security measures to keep pace with emerging threats. The multi-layered security framework protects data and communications between connected devices, increasing the overall resilience and reliability of IoT ecosystems.
Quantum-resistant Hash Functions
To ensure the validity and integrity of data transferred between Internet of Things devices, quantum-resistant hash functions are essential, particularly in light of the new risks posed by quantum computing. These hash functions are designed to withstand attempts to crack popular hash algorithms like SHA-256 or SHA-3 using the computing power of quantum computers. Organisations may fortify their data protection policies and preserve trust in IoT ecosystems despite the constantly evolving threat landscape posed by quantum technologies by incorporating quantum-resistant hash functions into IoT security protocols.
Organisations may reduce the risks associated with developments in quantum computing and ensure strong security for IoT applications, data transfers, and communication channels by leveraging these Quantum IoT improvements in cryptography.
How can Quantum Cryptography improve Data Privacy in IoT?
In Internet of Things (IoT) environments, quantum cryptography can greatly enhance data privacy by mitigating critical vulnerabilities and improving security protocols. This is what quantum cryptography does, in this way:
Unhackable Encryption
Quantum cryptography provides unhackable encryption techniques that fend off attacks from both classical and quantum computers. Quantum cryptography creates cryptographic keys that are intrinsically secure by utilising quantum concepts such as superposition and entanglement, in contrast to conventional cryptography techniques that rely on mathematical complexity. This guarantees the confidentiality and protection of data from unauthorised access during transmission between IoT devices.
Quantum Key Distribution (QKD)
One well-known quantum cryptography method for secure key sharing across Internet of Things devices is quantum key distribution. Using principles of quantum mechanics, QKD generates and distributes encryption keys in a verifiably secure manner. This makes it ideal for protecting communication channels in Internet of Things networks, as it removes concerns about key interception or eavesdropping.
Quantum-resistant Algorithms
Quantum-resistant algorithms for data encryption and authentication are encouraged by quantum cryptography. Traditional cryptographic methods can be broken by quantum computers, which is why these algorithms are designed to withstand such attacks. IoT devices can ensure long-term data privacy and security, even in the face of emerging quantum computing, by utilising quantum-resistant algorithms.
Tamper-proof Communication Channels
IoT devices can establish tamper-proof communication channels thanks to quantum cryptography. The detection of any attempt to intercept or tamper with data during transmission is guaranteed by quantum principles like quantum entanglement. This improves data interchange integrity and guards against illegal changes or additions to private data.
Enhanced Authentication and Access Control
In the context of the Internet of Things, quantum cryptography optimises authentication protocols and access control. Quantum-enhanced authentication protocols offer stronger identity verification and authorisation procedures, reducing the risk of unwanted access to IoT networks or devices. This ensures that only authorised parties can communicate with IoT systems, thereby protecting sensitive data.
By providing unhackable encryption, secure key distribution, quantum-resistant algorithms, tamper-proof communication channels, and enhanced authentication procedures, quantum cryptography significantly improves data privacy in the Internet of Things. IoT installations can achieve enhanced security, confidentiality, and reliability in data handling and communication by incorporating quantum cryptography techniques.
Benefits of Quantum IoT in Cryptography and Secure Communications
The quantum internet of things, or IoT, offers many advantages and the potential to transform secure communications and cryptography in several ways.
Unbreakable Encryption: The use of encryption techniques and quantum-resistant algorithms that are immune to attacks from quantum computers is enabled by quantum IoT. Quantum-resistant encryption is essential for protecting IoT communications, as traditional cryptographic techniques may be vulnerable to such attacks.
Enhanced Security: By utilising quantum concepts like quantum key distribution (QKD), quantum IoT improves security. Compared to traditional key exchange protocols, QKD offers a higher level of protection by identifying any unauthorised efforts to intercept or tamper with the keys, ensuring secure key exchange between devices.
Secure Authentication: Quantum concepts such as quantum fingerprints or quantum authentication tokens enable secure authentication processes in quantum IoT. These techniques improve the authentication process for IoT devices by leveraging quantum properties to generate unique IDs or tokens that are nearly impossible to copy or forge.
Improved Privacy: By providing quantum-safe protocols for data anonymisation and privacy-preserving computations, quantum IoT enhances privacy. These protocols address privacy problems in interconnected IoT ecosystems by enabling IoT devices to share and process data without jeopardising the confidentiality of sensitive information.
Resilience Against Quantum Attacks: Communication systems and cryptographic protocols are made more resilient against potential quantum attacks through quantum IoT. Quantum IoT protects IoT networks and communications infrastructure from new risks brought about by developments in quantum computing by incorporating security controls and quantum-resistant algorithms.
Reduced Latency: Secure connections between IoT devices can benefit from quantum communication techniques, reducing latency. Quantum IoT seeks to maximise data transmission speeds and reduce latency, improving real-time interactions and responsiveness in Internet of Things applications. It does this by utilising concepts of quantum entanglement and superposition.
Scalability and Efficiency: The increasing complexity and volume of data transferred between IoT devices are accommodated by the scalable, efficient design of quantum IoT solutions. Large-scale IoT deployment integration is enabled by effective key management and secure data transmission provided by quantum cryptography protocols.
Future-Proofing Security: By anticipating and mitigating potential risks arising from developments in quantum computing, quantum IoT future-proofs security protocols. Organisations can reduce the risk of quantum attacks and ensure long-term security for IoT deployments by implementing encryption and authentication methods that are resistant to quantum computing.
All things considered, quantum IoT offers increased security and privacy, enhanced resistance to quantum attacks, and paves the way for future-proof security measures in interconnected IoT ecosystems, which are crucial for cryptography and secure communications in IoT environments.
Potential Risks of not using Quantum Cryptography in IoT
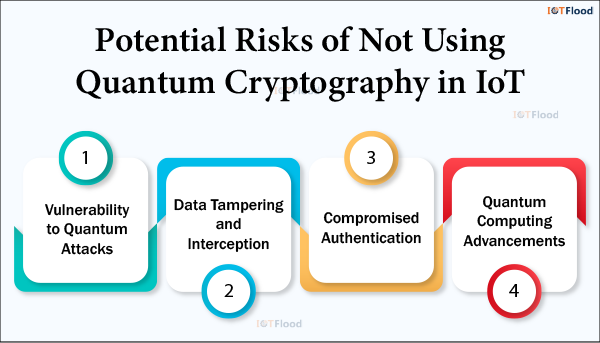
IoT deployments that do not use quantum cryptography risk exposing systems to various vulnerabilities and threats.
Vulnerability to Quantum Attacks: Classical cryptography techniques, including ECC and RSA, are susceptible to quantum-computer attacks. Sensitive information sent between IoT devices may be compromised if quantum-resistant encryption is not utilised. This is because adversaries may use quantum methods, such as Shor’s algorithm, to factor big numbers quickly.
Data Tampering and Interception: IoT communications are vulnerable to data tampering and interception in the absence of quantum-resistant encryption. The integrity and confidentiality of Internet of Things data can be compromised by adversaries who exploit flaws in traditional encryption systems to intercept conversations, modify transmitted data, or conduct man-in-the-middle attacks.
Compromised Authentication: Unauthorised access to Internet of Things devices and networks could result from a compromise in non-quantum-secure authentication methods. Adversaries pose serious security risks to IoT deployments by using flaws in authentication protocols to impersonate reputable devices, obtain unauthorised access, or insert malicious commands.
Privacy Breaches: Inadequate encryption in IoT communications can lead to privacy violations and data disclosure. Sensitive data shared between IoT devices, such as financial transactions, personal information, or proprietary company information, may be vulnerable to unauthorised access or disclosure in the absence of quantum-resistant privacy-preserving methods.
Quantum Computing Advancements: The possibility of quantum attacks against traditional cryptographic systems increases as quantum computing technologies advance. Future quantum attacks can compromise the long-term security and resilience of IoT networks and applications if quantum-resistant cryptography is not used in IoT installations.
IoT Device Compromise: IoT devices can be compromised and exploited through insecure communication pathways. Attackers can use cryptographic protocol flaws to launch denial-of-service attacks, take over IoT devices without authorisation, or interrupt vital activities by compromising system integrity.
Regulatory Compliance: Organisations implementing IoT solutions may face fines, legal repercussions, and reputational harm if they fail to comply with evolving security and privacy legislation, such as the CCPA, GDPR, or industry-specific standards, due to insufficient encryption.
Lack of Trust and Reliability: Unreliable connected systems and services suffer from insecure IoT connectivity. If users, companies, and stakeholders believe there are substantial security threats related to data protection, privacy, and confidentiality, they can be reluctant to embrace IoT technologies.
Organisations expose themselves to these threats by implementing IoT installations without quantum cryptography, endangering the security, privacy, and credibility of interconnected IoT ecosystems. To reduce these dangers and provide strong defence against new quantum threats, it is imperative to implement encryption and security mechanisms that are resistant to quantum computing.
Potential quantum Computing Attacks on IoT Devices and their Consequences
The potential for quantum computing attacks to undermine cryptographic protocols and exploit weaknesses in interconnected systems makes them a serious threat to Internet of Things devices. These are some possible IoT device quantum computing attacks and their repercussions:
Shor’s Algorithm Attack
- Consequence: RSA and ECC cryptographic techniques, which are frequently used for secure communication in IoT devices, can be broken by Shor’s algorithm, which can factor large numbers quickly.
- Impact: Unauthorised access to sensitive data, such as login credentials or critical command instructions, can be obtained by attackers who can decrypt encrypted Internet of Things connections and jeopardise data confidentiality.
Grover’s Algorithm Attack
- Consequence: Grover’s approach reduces the required key size for symmetric encryption algorithms by speeding up brute-force key searches.
- Impact: Faster key-search attacks enable attackers to reduce the security margin of symmetric encryption systems used to safeguard Internet of Things data, potentially resulting in data breaches, manipulation, or unauthorised access.
Quantum Replay Attacks
- Consequence: By recording and replaying quantum states, quantum replay attacks exploit flaws in cryptographic methods, including challenge-response authentication.
- Impact: Bypassing authentication procedures, replaying intercepted quantum states to obtain unauthorised access, or impersonating real IoT devices, attackers can jeopardise system security and integrity.
Quantum Side-Channel Attacks
- Consequence: By utilising quantum phenomena to retrieve sensitive data, quantum side-channel attacks target physical weaknesses and implementation errors in Internet of Things devices.
- Impact: Through quantum side channels, attackers can obtain cryptographic keys, device identifiers, or sensitive data from Internet of Things devices, jeopardising security measures for data integrity, secrecy, and privacy.
Quantum Cryptanalysis Attacks
- Consequence: Cryptographic primitives and protocols used in Internet of Things security are broken by quantum-cryptanalysis attacks that leverage quantum algorithms.
- Impact: Sophisticated adversaries can launch attacks against IoT encryption systems, jeopardising authentication procedures, data confidentiality, and overall system security. This could result in device compromise or data breaches.
Quantum Key Distribution (QKD) Exploitation
Consequence: Secure key exchange between IoT devices may be compromised if vulnerabilities in quantum key distribution protocols are exploited.
Impact: Unauthorised access, data manipulation, or eavesdropping may result from attackers’ ability to intercept or modify quantum keys that are exchanged between Internet of Things devices, jeopardising the confidentiality and integrity of communications.
Quantum-enhanced DoS attacks
- Consequence: Denial-of-service (DoS) attacks on Internet of Things networks and infrastructure can become more effective with the use of quantum computing capabilities.
- Impact: With the use of quantum resources, attackers can mount potent denial-of-service (DoS) assaults that disrupt Internet of Things (IoT) services, clog networks, and hinder device functionality, all of which can result in service interruptions and operational disruptions.
Strong quantum-resistant security solutions, such as secure key management, authentication protocols, quantum-resistant encryption, and quantum-safe cryptography standards, are desperately needed in light of attacks using quantum computing against Internet of Things devices. Serious repercussions could arise from ignoring these dangers, including compromised devices, unauthorised access, data breaches, operational disruptions, and a decline in public confidence in IoT ecosystems.
Real-World Applications
There are numerous practical uses of the quantum Internet of Things (IoT) for cryptography and secure communications across a variety of sectors. Here are a few instances:
Secure Data Transmission: In industries such as finance, healthcare, and defence, quantum IoT can be used to secure data transmission between IoT devices and centralised systems—quantum encryption techniques ensure secure transmission, shielding data from interception by malicious actors.
IoT Device Authentication: By leveraging quantum-resistant authentication protocols, quantum IoT can enhance device authentication. By limiting the availability of unauthorised devices to IoT networks, this mitigates the danger of data breaches and unauthorised access.
Supply Chain Security: By enabling secure communication and data exchange among IoT-enabled devices, warehouses, transportation systems, and stakeholders, quantum IoT can enhance supply chain security. This lessens the possibility of sensitive supply chain data being altered, counterfeited, or accessed by unauthorised parties.
Healthcare Data Privacy: The security and privacy of healthcare data transferred between IoT devices, medical equipment, and electronic health record systems can be significantly enhanced by quantum IoT. Ensuring patient confidentiality and adhering to data protection standards are of utmost importance.
Smart Grid Security: By leveraging quantum-resistant encryption and authentication, quantum IoT in the energy sector could enhance smart grid security. This helps guard against cyberattacks and unauthorised access to vital infrastructure, including distribution networks, power generation systems, and Internet of Things devices.
Smart Home Security: By protecting communication between IoT devices, home automation systems, and cloud services, quantum IoT can enhance the security of smart homes. Sensitive information, including personal data, home security alarms, and video surveillance recordings, is protected against hackers and attackers through quantum encryption.
Financial Transactions: Using IoT equipment like automated vending machines, linked cars for toll collection, and payment terminals, quantum IoT can be utilised to secure financial transactions. By ensuring the security and integrity of economic data, quantum cryptography lowers the possibility of fraud and unauthorised access.
Industrial Control Systems (ICS) Security: Critical infrastructure, manufacturing, and utilities all employ industrial control systems (ICS), which can be made more secure by using quantum IoT. Quantum IoT guards against cyberattacks and unauthorised manipulation of sensors, communication channels, and ICS components by utilising quantum-resistant authentication and encryption algorithms.
The applications above showcase the potential of Quantum IoT in cryptography and secure communications to address cybersecurity issues and safeguard confidential information across diverse industries that utilise IoT technologies.
Challenges and Considerations
Here are some additional issues and considerations for Quantum IoT:
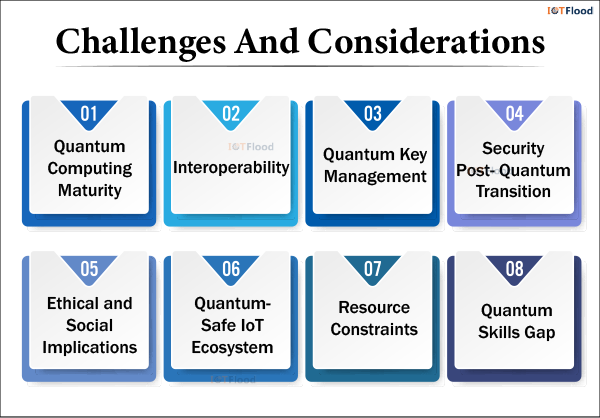
Quantum Computing Maturity: As this technology continues to advance, more work is needed to ensure performance and reliability across quantum algorithms, hardware, and software for Internet of Things applications.
Interoperability: Standardised protocols and interfaces are necessary to ensure interoperability between Quantum IoT systems and current IoT platforms, but achieving this can be difficult.
Quantum Key Management: In large-scale Internet of Things deployments, managing quantum keys for encryption and authentication requires reliable key management systems that securely handle distribution, storage, and revocation.
Resource Constraints: Because IoT devices often have limited computing power and energy, implementing quantum algorithms and cryptographic protocols—which require substantial RAM and processing power—can be difficult.
Security Post-Quantum Transition: To maintain long-term security, post-quantum cryptography (PQC) must replace classical cryptographic techniques as quantum computing improves. This changeover process can be intricate, necessitating meticulous preparation and cooperation.
Ethical and Social Implications: Concerns about data privacy, surveillance, and the societal effects of quantum technologies are among the ethical and social issues raised by the Internet of Things. Public involvement, openness, and moral frameworks are necessary to address these issues.
Quantum-Safe IoT Ecosystem: To create standards, best practices, and guidelines for protecting IoT deployments against quantum risks, industry, academia, and policymakers must work together.
Quantum Skills Gap: To drive innovation and overcome technical obstacles in Quantum IoT deployments, it is imperative to develop and sustain a workforce with experience in both IoT and quantum computing technologies.
To fully realise the potential of Quantum IoT to improve cybersecurity and data protection in IoT ecosystems, stakeholders must address these issues and concerns.
Future Prospects
Quantum IoT holds great potential and offers numerous opportunities to transform secure communication in the Internet of Things (IoT). Even with obstacles, including integration complexity and financial concerns, it is anticipated that continued research and technological developments will lower costs and increase the accessibility of Quantum Key Distribution (QKD) technology across a broader range of industries and applications. Quantum IoT can raise the bar for security and trust in IoT ecosystems as quantum computing advances and standardises quantum-resistant cryptographic techniques.
Overcoming technological obstacles and building strong frameworks for Quantum IoT adoption will require cooperation between researchers, industry leaders, and legislators. Through partnership, it may be possible to create best practices, standardised protocols, and legal rules that guarantee security, privacy, and interoperability among various IoT implementations. Furthermore, to drive innovation and realise the full potential of Quantum IoT in protecting connected devices and data, it will be imperative to cultivate a workforce with quantum skills through education and training programmes.
Quantum IoT offers previously unheard-of levels of security, privacy, and trust, signalling a fundamental shift in how the IoT ecosystem is secured. Quantum IoT opens the door to a future where IoT devices connect and exchange data with confidence, are resilient against quantum attacks, and build on a foundation of collaboration and innovation, driving progress by utilising concepts from quantum mechanics.
Conclusion
At the vanguard of cybersecurity, quantum IoT offers a ground-breaking method for data protection and encryption in IoT networks. Quantum physics can help enterprises improve data security to previously unheard-of heights while ensuring the validity, integrity, and confidentiality of Internet of Things communications. As quantum IoT technologies advance, they will play a significant role in shaping how secure communications in networked digital environments will develop.
In the future, the ongoing development of Quantum IoT offers significant potential for addressing the ever-changing cybersecurity challenges. Organisations may future-proof their systems against potential quantum vulnerabilities and protect their IoT infrastructure from current threats by implementing quantum-enhanced encryption and security measures. This proactive strategy ensures that IoT networks remain robust and uphold the highest standards of data protection as quantum computing capabilities advance. Therefore, Quantum IoT is not only a technological breakthrough but also a strategic necessity for businesses looking to prosper in a world that is increasingly data-driven and networked.