Quantum Computing and IoT
At the forefront of technological advancement, quantum computing offers a paradigm shift in computational capability that has the potential to transform a wide range of sectors completely. The Internet of Things (IoT) is one of these revolutionary realms, where quantum computing and IoT technologies come together to provide enormous promise. In this piece, we explore the significant effects that quantum computing may have on data processing and Internet of Things security. Our goal is to discover how quantum computing might change the fundamental structure of data analytics frameworks and cybersecurity tactics in the Internet of Things ecosystem by investigating the connections between these innovative domains.
The union of quantum computing and the Internet of Things (IoT) brings together previously unheard-of processing power and the enormous interconnectivity of digital objects and data. The potential of quantum computing to enhance data processing in Internet of Things applications and strengthen security protocols is becoming increasingly apparent as it develops and becomes more widely available. This investigation delves into the complex dynamics of quantum-powered systems. It provides an overview of the possible future developments for IoT-driven enterprises, including how they will handle data protection and analytical insights.
Understanding Quantum Computing
Superposition and entanglement are fundamental ideas in quantum computing. Qubits can exist in numerous states concurrently thanks to superposition, significantly increasing the possibilities for computation. Contrarily, entanglement connects the states of qubits, allowing them to communicate across distances instantly. Quantum computers can handle complicated problems at a pace and scale never seen before because of these quantum phenomena.
Definition
Quantum computing is a cutting-edge computing paradigm that applies quantum mechanics concepts to conduct sophisticated calculations and solve issues that classical computers cannot handle. Quantum bits, or qubits, are the fundamental building blocks of quantum computing. Superposition allows qubits to exist in several states at once. Because of this special characteristic, quantum computers may simultaneously explore large solution spaces, resulting in exponential computational power and previously unheard-of efficiency for solving complex problems.
Qubits are different from classical bits in that they can concurrently be in a superposition of both 0 and 1 states, representing information as either 0 or 1. Quantum computers can handle enormous volumes of data in parallel thanks to this superposition, which provides a quantum increase in processing speed and capacity. Furthermore, qubits can correlate with one another according to the phenomenon of entanglement, which makes it possible for information to be sent instantly between qubits even when they are physically separated.
Cryptography, for example, is a significant application of quantum computer technology. Theoretically, by rapidly factoring large numbers essential to standard cryptographic techniques like RSA encryption, quantum computers may crack these approaches. To protect sensitive information and communications from the disruptive potential of quantum computing, research on quantum-resistant cryptography has been sparked.
Principles of Quantum Computing
Several fundamental ideas from quantum mechanics serve as the foundation for quantum computing. These basic ideas set quantum computers apart from traditional computers and serve as the foundation for their operation.
The underlying ideas of quantum computing are as follows:
Superposition
Superposition is a fundamental concept in quantum computing. Bits can be in one of two states in classical computing: 0 or 1. Qubits, or quantum bits, can, nevertheless, concurrently exist in a superposition of 0 and 1 in quantum computing. Because a qubit may represent numerous states simultaneously, quantum computers can do concurrent computations and explore an extensive array of possibilities.
Entanglement
Another fundamental idea in quantum computing is entanglement. Quantum entanglement occurs when two qubits, independent of their physical distance from one another, exhibit correlated states. Quantum computers can operate and communicate in ways that classical computers cannot due to entanglement. Fast information transfer and correlation are made possible by the instantaneous state change of an entangled qubit upon modification.
Quantum gates
In a quantum computer, quantum gates are operations that change the state of qubits. The Hadamard gate, CNOT gate, phase gate, and other gates are examples of these gates. Quantum gates employ the concepts of superposition and entanglement to manipulate and process qubit data. It is possible to create quantum algorithms that effectively solve particular computational problems by applying sequences of quantum gates.
Measurement
An essential component of quantum computing is measurement. A qubit’s superposition collapses upon measurement, and it assumes a determinate state (either 0 or 1) according to the probabilities determined by its superposition state. To acquire the outcome of a quantum algorithm and to extract meaningful information from quantum calculations, a measurement procedure is necessary.
Quantum Parallelism
By utilising quantum parallelism, quantum computers can analyse and investigate several computational paths at once. When compared to conventional computing, which uses sequential operations, this parallelism results in exponential speedups for specific problem types.
Quantum Uncertainty and Probability
Quantum computing is subject to probabilistic outcomes and uncertainty arising from quantum mechanics. Because of the nature of superposition and measurement, quantum computing produces probabilistic results, in contrast to traditional computing, which functions deterministically. Quantum factorisation algorithms and quantum simulation tasks are two examples of how quantum algorithms frequently take advantage of probabilistic processes to achieve computational advantages.
Together, these ideas allow quantum computers to solve complicated tasks faster than classical computers in some situations, potentially leading to breakthroughs in fields like cryptography, optimisation, simulation, and machine learning. But to fully utilise quantum computing, obstacles, including those about qubit coherence, error correction, and quantum system scaling, must be overcome. The goal of ongoing research and development is to advance quantum computing technologies and realise their transformational potential.
Working
Utilising the ideas of quantum mechanics to carry out computations, quantum computing operates in a fundamentally different way from classical computing. The following are the main ideas that drive quantum computing:
Qubits: The fundamental unit of information used by quantum computers is the quantum bit, or qubit. Qubits can simultaneously exist in a superposition of 0 and 1, in contrast to classical bits, which can only be either 0 or 1. For some types of problems, this superposition allows quantum computers to perform multiple computations simultaneously, resulting in exponential computational speedups.
Superposition: Superposition is a key notion in quantum physics that allows particles such as qubits to exist in numerous states simultaneously. Accordingly, until a qubit is measured, it can concurrently represent 0 and 1, after which it will collapse to one of the potential states. Quantum computers may investigate a vast number of possible answers at once thanks to superposition, greatly accelerating some types of computations.
Entanglement: Entanglement is an essential feature of quantum computing. When two qubits entangle, their states are interdependent and do not depend on one another’s physical distance from one. This enables fast correlation and communication between qubits in a quantum system since modifications to one qubit instantly impact the state of the entangled qubit.
Quantum gates: In a quantum computer, quantum gates are operations that change the state of qubits. These gates are capable of entangling qubits, altering their superposition, and carrying out other mathematical operations that are essential for quantum computations. Sequences of these quantum gates are used to build quantum algorithms that efficiently tackle particular kinds of problems.
Measurement: A critical step in quantum computing, reducing the superposition of qubits into distinct states. A qubit collapses to 0 or 1 when measured, depending on the probabilities determined by its superposition state. To obtain the outcome of a quantum computation, a measurement procedure is necessary.
Quantum computing algorithms use these ideas to handle challenging issues that are computationally demanding for conventional computers, like quantum simulations, cryptography, and optimisation. But quantum computing is still in its infancy, and creating scalable, dependable quantum computers capable of carrying out practical computations is still a formidable obstacle. The discipline is moving closer to achieving the full potential of quantum computing through ongoing research and development in quantum hardware, quantum algorithms, and error correction methods.
How does it differ from Classic Computing?
Using qubits and the concepts of quantum physics are two of the main ways in which quantum computing differs from classical computing. The following are the primary distinctions between classical and quantum computing:
Basic Units of Information
- Classical Computing: In classical computers, bits are the fundamental building blocks of information. A bit can be either a 0 or a 1.
- Quantum computing: Qubits, which are particles that exhibit superposition, are the building blocks of quantum computers. Until it is measured, a qubit can simultaneously represent 0 and 1.
Superposition
- Classical Computing: Only one state—0 or 1—can exist for a classical bit at a time.
- Quantum computing: Qubits can represent several possibilities at once by existing in a superposition of states. This allows massively parallel computations to be carried out by quantum computers.
Entanglement
- Classical Computing: In classical computing, bits don’t show entanglement and are independent of one another.
- Quantum computing: Qubits can entangle, which means that even if they are physically separated, the state of one qubit depends on the state of another. In a quantum system, entanglement allows for quick correlation and communication between qubits.
Processing Power
- Classical Computing: For some kinds of tasks, the computing performance of classical computers is limited because they handle information in a sequential, step-by-step manner.
- Quantum Computing: Because of superposition and entanglement, quantum computers can handle enormous amounts of data in parallel. This results in exponential speedups for particular kinds of calculations, such as factorisation or optimisation of quantum algorithms.
Algorithmic Approach
- Classical Computing: Classical algorithms are based on classical logic gates, such as AND, OR, and NOT gates, and are designed to operate sequentially.
- Quantum computing: Quantum gates, such as the Hadamard, CNOT, and phase gates, are used to manipulate qubits in the creation of quantum algorithms. Utilising superposition and entanglement, these quantum gates enable computations that make use of quantum parallelism.
Measurement and Collapse
- Classical Computing: Bits in classical computing are always in one of two states (0 or 1), and measurements do not affect their state.
- Quantum Computing: A qubit’s superposition collapses to a definite state (0 or 1) when it is measured in a quantum system, depending on the probabilities determined by its superposition state. To determine the outcome of a quantum computation, this measuring procedure is necessary.
All things considered, quantum computing offers the potential for exponential speedups and the ability to solve challenging problems that are beyond the capabilities of conventional computers at this time. Quantum computing is still in its infancy, though, and there are still issues to be resolved with qubit coherence, error correction, and scalability. Advancements in research and development are propelling quantum computing towards real-world applications in diverse industries and scientific fields.
A Double-Edged Sword: Power and Peril
Utilising the mysterious ideas of quantum mechanics, quantum computing offers a revolutionary advance in computational power, enabling the solution of issues that have long baffled classical computers.
The potential for quantum computing to transform the Internet of Things (IoT) entirely is awe-inspiring. With the potential to revolutionise data analytics from connected devices, quantum algorithms could lead to more intelligent systems and more effective operations that can extract more profound insights from the vast amount of data created by the Internet of Things.
But this promise of power comes with a serious risk. The very property that makes quantum computers so powerful—their ability to factor big numbers quickly—also presents a serious risk to the encryption techniques that operate as bulwarks protecting our private information. The robustness of current encryption algorithms against brute force assaults from classical computers stems from their reliance on the computational difficulties of factoring huge integers. However, the development of a strong enough quantum computer might weaken these cryptographic locks and expose a plethora of private data sent by Internet of Things devices, from vital medical equipment like pacemakers to residential thermostats.
This paradox captures the dual character of quantum computing in the context of data processing and security for the Internet of Things (IoT): it is a two-edged sword where unmatched computational power entangles with impending vulnerabilities, necessitating a careful examination of the benefits and drawbacks of the quantum revolution in IoT security.
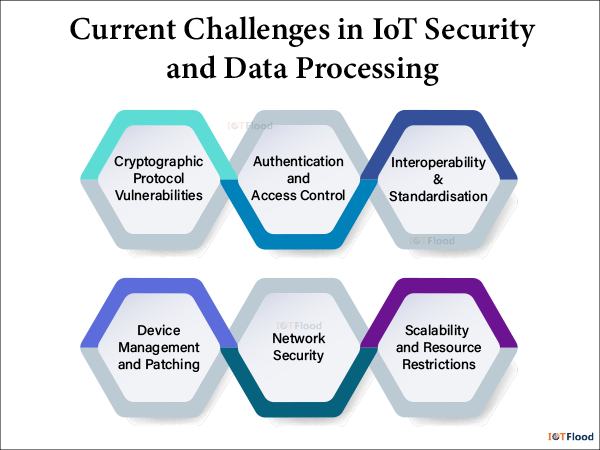
Current Challenges in IoT Security and Data Processing
Cryptographic Protocol Vulnerabilities: Replay and man-in-the-middle attacks are two common ways that traditional cryptographic protocols, like SSL/TLS, used in Internet of Things devices, might be compromised. Because Internet of Things devices frequently have low processing and memory capacities, it can be not easy to install strong encryption.
Authentication and Access Control: It is essential to ensure that IoT devices have secure access control and authentication systems. Attackers may use weak authentication procedures or default credentials to obtain unauthorised access to private information or device control.
Data Privacy Concerns: IoT devices capture massive volumes of data, including personally identifiable and sensitive information. A significant difficulty in IoT environments is ensuring data privacy through encryption, anonymisation, and secure data storage, especially given the variety of data types and formats.
Device Management and Patching: It can be challenging to manage a large number of IoT devices that are dispersed throughout several locations. It can be difficult to properly manage the timely installation of firmware upgrades, security patches, and software updates that reduce vulnerabilities.
Network Security: Since Internet of Things (IoT) devices frequently communicate via wireless networks, they are vulnerable to network-based attacks such as denial-of-service (DoS) attacks, eavesdropping, and spoofing. Strong encryption, intrusion detection systems, and network segmentation to separate important devices are necessary for IoT network security.
Interoperability & Standardisation: Interoperability is an issue due to the variety of IoT devices from different manufacturers and the absence of standardised security standards. It is challenging to provide smooth data transmission and communication amongst heterogeneous devices while upholding security requirements.
Supply Chain Risks: Several suppliers, independent parts, and firmware dependencies are all part of the supply chain for Internet of Things devices. It is imperative to ensure supply chain security, including secure boot procedures, firmware verification, and vendor risk mitigation, to avert manipulation and malicious assaults at the device level.
Scalability and Resource Restrictions: Internet of Things implementations frequently entail a multitude of devices with disparate computational capacities and resource limitations. It can be challenging to implement security mechanisms that are scalable, effective, and resource-friendly, particularly for devices with limited resources like sensors and actuators.
Regulatory Compliance: Adhering to industry standards and data protection laws (such as GDPR, HIPAA, and ISO/IEC 27001) raises additional challenges for IoT security. For Internet of Things deployments, ensuring compliance with legal requirements while upholding security and data privacy standards presents a constant challenge.
A comprehensive strategy that includes secure design principles, strong encryption techniques, efficient access control, ongoing monitoring, and frequent security audits is needed to address these issues. Working together, stakeholders—device makers, IoT service providers, cybersecurity specialists, and regulatory agencies—is crucial to addressing the constantly changing threat landscape and improving the security posture of IoT ecosystems.
Quantum Computing and IoT
A revolutionary paradigm change in computing and communication is being brought about by the convergence of quantum computing with the Internet of Things (IoT). IoT ecosystems are data-intensive, and quantum computing’s capacity to handle enormous volumes of data in parallel and effectively solve complicated issues complements this feature. Through this integration, there are more opportunities for improved resource management, real-time processing, and data analytics in Internet of Things networks.
IoT security and encryption are important areas of influence. The development of cryptographic algorithms resistant to quantum assaults is being undertaken to strengthen Internet of Things communications. This development is essential for guaranteeing the privacy, integrity, and confidentiality of IoT data, particularly in vital industries like finance, healthcare, and smart infrastructure.
Furthermore, improvements in edge computing capabilities may result from the interaction of quantum computing and IoT. The ability to carry out complex calculations locally on quantum-enhanced edge devices lowers latency, boosts responsiveness, and allows real-time decision-making in Internet of Things applications. This distributed computing approach opens the door for creative solutions in a range of industries by improving the scalability, dependability, and efficiency of operating IoT networks.
Network Optimisation in IoT Using Quantum Computing
The potential of quantum computing greatly enhances the field of Internet of Things (IoT) network optimisation. Its ability to perform intricate computations and algorithms that traditional computing finds difficult, particularly in dynamic and data-intensive Internet of Things situations, is one of its main advantages. By lowering latency, assuring effective data transmission pathways, and dynamically adjusting to network changes, quantum algorithms have the potential to transform routing systems completely. In addition to improving network performance, this optimised routing also helps reduce energy consumption and increase scalability—two crucial aspects in the Internet of Things, where billions of devices are linked together.
Moreover, quantum computing offers Internet of Things networks never-before-seen degrees of security. Sensitive data transferred between IoT devices is protected by quantum cryptography techniques like Quantum Key Distribution (QKD), which offer unbreakable encryption solutions. As IoT networks handle more sensitive data from a broader range of businesses, including finance and healthcare, this quantum-resistant security becomes even more critical. Quantum-enhanced security strengthens data integrity and confidentiality, thereby reducing the risk of cyber attacks and unauthorised access and promoting confidence in IoT environments.
Furthermore, the fault tolerance of quantum computing plays a crucial role in maintaining the ongoing functioning of Internet of Things systems. Quantum error correction methods handle environmental disturbances and hardware malfunctions to keep networks reliable even in difficult situations. For mission-critical IoT applications where downtime can have profound effects, such as innovative infrastructure management, industrial automation, and healthcare monitoring, this resilience is essential. The robustness and continuity provided by quantum-enabled fault tolerance mechanisms improve the overall reliability of IoT networks.
Finally, real-time analytics, machine learning inference, and predictive modelling are made possible by the acceleration of data processing brought about by quantum computing in IoT environments. IoT applications can quickly obtain actionable insights due to their speed and efficiency, which promotes well-informed decision-making and operational enhancements. Quantum-enhanced data processing capabilities are essential for deriving value from the massive amounts of data generated by the Internet of Things as it continues to develop. IoT networks can leverage the computational power of quantum computing to open up new possibilities and spur innovation in a variety of industries.
Quantum Digital Marketing
At the nexus of marketing tactics and quantum computing, quantum digital marketing is an interesting new frontier. Four main ways that quantum computing can transform digital marketing are as follows:
Advanced Data Analytics
The unmatched processing power of quantum computing allows for the high-speed and accurate analysis of large amounts of data. Marketing campaigns can be more precisely targeted and individualised due to this capability, which provides marketers with a deeper understanding of consumer behaviour, preferences, and trends. The efficacy of marketing efforts can be increased by using quantum algorithms to find hidden correlations, recognise intricate patterns in data sets, and more precisely forecast client behavior.
Enhanced Personalisation
By using quantum algorithms to analyse enormous volumes of client data in real time, quantum computing can power hyper-personalised marketing campaigns. This makes it possible for marketers to present offers, recommendations, and information that are specifically catered to the tastes, actions, and buying habits of each customer. Brands may enhance client connections, increase engagement, and boost conversion rates by offering a more tailored and pertinent experience.
Optimised Campaign Optimisation
By doing simulations and scenario evaluations at a never-before-seen scale and speed, quantum computing can optimize marketing campaign plans. Marketers can adjust campaign parameters based on quantum-powered predictive modeling and optimisation algorithms, including ad placement, messaging, timing, and targeting. As a result, campaigns become more successful and efficient, increasing ROI and fostering business expansion.
Quantum-Secure Data Protection
Quantum computing also provides quantum-resistant encryption techniques that can protect critical consumer data and marketing insights, which is particularly relevant given the growing concerns about data privacy. Unbreakable encryption is provided by quantum cryptography techniques like Quantum Key Distribution (QKD), which also ensures data integrity and secrecy, shielding data from quantum attacks. Customers’ trust in brands is bolstered by this quantum-enhanced security, which is essential for upholding brand reputation and adhering to data protection laws.
Data scientists, marketers, and quantum experts must work together to integrate quantum computing into digital marketing. The potential for driving innovation, enhancing consumer experiences, and improving marketing success in the digital era is enormous when quantum computing is included in digital marketing strategies, as it continues to develop.
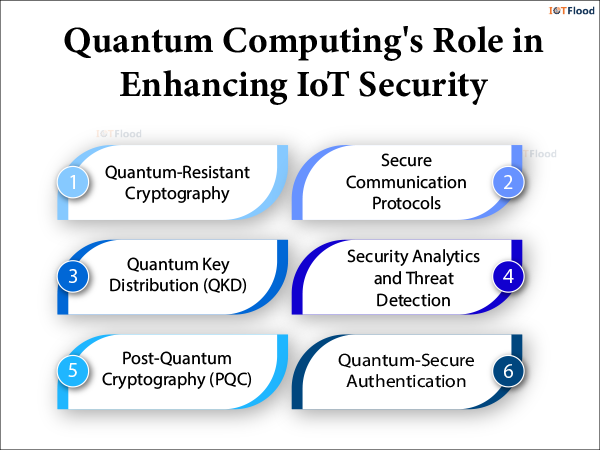
Quantum Computing’s Role in Enhancing IoT Security
IoT security could be significantly improved by quantum computing, thanks to several procedures and protocols designed to address the shortcomings and challenges of conventional cryptography techniques. The following are some significant ways that IoT security can be improved by quantum computing:
Quantum-Resistant Cryptography
Encryption is one of the most essential components of Internet of Things security. The creation and application of cryptographic algorithms resistant to quantum computer attacks can be aided by quantum computing. The efficacy of quantum computers in solving discrete logarithm issues and factoring large numbers is demonstrated by their efficiency in performing Shor’s algorithm and other traditional cryptography techniques like RSA and ECC. Quantum-resistant algorithms, such as hash-based signatures and lattice-based cryptography, provide strong security against quantum assaults and guarantee the integrity and confidentiality of data transferred between IoT devices.
Quantum Key Distribution (QKD)
The use of quantum key distribution protocols, such as BB84 and E91, for safe key exchange across Internet of Things devices is made possible by quantum computing. To safely create and distribute cryptographic keys, QKD makes use of quantum mechanical concepts, including quantum entanglement and the Heisenberg uncertainty principle. QKD is ideal for safeguarding communication channels in IoT networks because it offers unconditional security by detecting any attempts to intercept or tamper with quantum keys, unlike classical key exchange systems that are vulnerable to eavesdropping and interception.
Secure Communication Protocols
Explicitly developed for Internet of Things contexts, quantum computing can aid in the creation of quantum-safe communication protocols. To secure data transferred between IoT devices and cloud platforms, these protocols include authentication, integrity verification, and encryption that is resistant to quantum errors. Organisations can improve the overall security posture of IoT installations by reducing the risk of data breaches, man-in-the-middle attacks, and unauthorised access by incorporating quantum-safe protocols into IoT communication stacks.
Post-Quantum Cryptography (PQC)
The development of post-quantum cryptography (PQC) standards, which can fend off quantum attacks, is accelerated by quantum computing. PQC is a broad category of cryptographic algorithms that provide resistance against quantum algorithms such as Shor’s algorithm. Organizations may ensure long-term security for IoT devices and networks by implementing PQC algorithms in IoT security protocols. This will help organizations future-proof their systems against upcoming quantum attacks.
Quantum-Secure Authentication
The creation of quantum-resistant authentication techniques, including safe digital signatures and authentication protocols built with quantum-resistant algorithms, is made possible by quantum computing. By thwarting spoofing, impersonation, and illegal access, these authentication techniques improve the identity verification process for Internet of Things devices. Organizations may guarantee trustworthiness and integrity in data exchanges and device-to-device connectivity by integrating quantum-secure authentication into IoT networks.
Tamper-Resistant Hardware
The development and application of tamper-resistant hardware solutions for Internet of Things (IoT) devices can also benefit from quantum computing. By producing distinct IDs, cryptographic keys, and unpredictable randomness, quantum-based physical unclonable functions (PUFs) and quantum random number generators (QRNGs) might improve device security by lowering the risk of hardware-based attacks, counterfeiting, and tampering.
Security Analytics and Threat Detection
By utilising quantum algorithms for anomaly detection, pattern recognition, and real-time network activity monitoring, quantum computing can expedite security analytics and threat detection in Internet of Things environments. IoT infrastructures can benefit from proactive defence mechanisms against cybersecurity threats, including malware, botnets, and insider assaults, which can be identified and mitigated using quantum-enhanced machine learning algorithms.
Organizations can enhance the security of the Internet of Things (IoT) by utilizing quantum computing capabilities. This can be achieved by protecting confidential information, guaranteeing secure communication, and lessening the impact of quantum computing threats on networks and linked devices. Establishing strong standards for secure IoT deployments and promoting innovation in quantum-enhanced security solutions requires cooperation between researchers, industry stakeholders, and the government.
Quantum Computing’s Impact on IoT Data Processing
IoT data processing could be entirely transformed by quantum computing, which uses its powerful processing capacity and sophisticated algorithms to perform difficult data analytics jobs more effectively. The following are some ways that IoT data processing may be impacted by quantum computing:
Faster Data Processing
Compared to traditional computers, quantum computing can perform some calculations and data processing operations ten times faster. This speed advantage is beneficial for the real-time processing of massive amounts of data provided by the Internet of Things. Large-scale datasets may be analysed and insights extracted using quantum algorithms, which speed up response times and decision-making for Internet of Things applications.
Complex Data Analysis
Sensor readings, pictures, multimedia material, and time-series data are just a few examples of the diverse and complex structures frequently found in IoT data. The intricacy of IoT data may be handled by quantum algorithms, such as quantum machine learning algorithms and quantum clustering algorithms, which are more adept than classical computers at spotting patterns, correlations, anomalies, and trends. In Internet of Things situations, this feature improves the precision and level of detail in data analysis.
Optimized Resource Allocation
In the Internet of Things systems, quantum computing can improve resource usage and allocation. IoT resource management optimization issues, such as energy optimization, route optimization, supply chain optimization, and workload scheduling, can be handled using quantum optimization algorithms, such as quantum annealing and quantum-inspired optimization techniques. IoT implementations can gain improved performance, economy, and efficiency by optimizing resource allocation.
Real-time Predictive Analytics
By utilizing quantum machine learning models and algorithms, quantum computing makes real-time predictive analytics possible in Internet of Things applications. Based on streaming IoT data, these models can foresee patterns, identify anomalies, and predict future consequences. In dynamic IoT environments, real-time predictive analytics enables organisations to make better decisions, streamline workflows, and proactively spot possible problems.
Improved Data Security
In IoT data processing pipelines, quantum computing can improve data security. Sophisticated encryption algorithms that are immune to quantum-powered attacks can shield critical Internet of Things data, guaranteeing authenticity, secrecy, and integrity for the duration of the data’s life cycle. In addition to identifying cybersecurity risks and weaknesses in Internet of Things networks, quantum-enhanced security analytics also improve overall data protection and threat mitigation capabilities.
Scalable Data Analytics
For Internet of Things applications, quantum computing provides scalability in data analytics. Quantum computers offer scalable solutions for IoT data processing and analysis, enabling them to manage computational workloads and datasets that are expanding exponentially. For Internet of Things deployments that need to analyze data from numerous devices, sensors, and sources dispersed across various locations, this scalability is essential.
Advanced Modelling and Simulation
In Internet of Things applications, quantum computing can help with enhanced modeling and simulation. Complex systems, physical phenomena, and IoT-related processes like smart grids, logistics, healthcare, and manufacturing can all be modeled and optimized via quantum simulations. Organisations can test scenarios, assess approaches, and replicate real-world conditions for Internet of Things installations through the use of quantum simulations.
Data Fusion and Integration
By merging disparate data sources, formats, and protocols, quantum computing can facilitate data fusion and integration in Internet of Things ecosystems. IoT devices, cloud platforms, edge nodes, and external sources can integrate data with quantum algorithms, enabling complete data fusion for comprehensive insights and decision-making. This integration improves the connectivity and interoperability of IoT systems.
Organizations may unlock new possibilities in IoT data processing, such as greater security, scalability, faster analysis, and advanced predictive capabilities, by utilizing the power of quantum computing. Future IoT data processing will be shaped by cooperative research and development activities in quantum-enhanced data analytics. These initiatives will continue to spur innovation.
The Race Against Time: Securing the Quantum Future
The impending threat that quantum computing poses to established cryptography techniques has prompted a vital race against time to secure the quantum future. The cryptographic methods that are the foundation of contemporary security are vulnerable to hacking as quantum computing develops. Fortunately, there’s good news: post-quantum cryptography (PQC) specialists and researchers are actively tackling this difficulty.
PQC is devoted to creating new cryptographic protocols and algorithms that withstand attacks from quantum computers. These include algorithms that can effectively crack conventional encryption techniques, such as Shor’s algorithm. Even in a computing environment powered by quantum technology, the confidentiality, integrity, and validity of data are guaranteed by these new PQC algorithms, which are built to withstand quantum attacks. Furthermore, standardisation procedures are being carried out on these algorithms, opening the door for their integration into future IoT systems and gadgets. The cybersecurity community is proactively securing the quantum future and protecting private data in IoT ecosystems from new threats by adopting PQC.
Real-World Applications
The revolutionary potential of these technologies is demonstrated by the numerous industries and fields in which real-world applications of quantum computing and IoT integration are used:
Healthcare and Medical Research
By enabling personalized treatment regimens, sophisticated medical diagnostics, and drug development, quantum-enhanced IoT has the potential to transform the healthcare industry completely. Quantum algorithms are capable of identifying biomarkers, analyzing genomic data, and optimizing patient treatment plans. Quantum computing-enabled Internet of Things (IoT) devices can track vital signs, evaluate patient data in real time, and enable remote healthcare services with improved confidentiality and privacy.
Urban infrastructure and smart cities
IoT solutions driven by quantum technology can improve the sustainability and efficiency of innovative city projects. Integrated sensors, actuators, and Internet of Things (IoT) devices can monitor air quality, control waste disposal systems, optimize traffic management, and use less energy. Real-time analytics, predictive modeling, and decision-making for smart city operations are made possible by quantum computing, which enhances resource efficiency and quality of life.
Manufacturing and Industry 4.0
Applications of quantum-enhanced IoT technologies in manufacturing and Industry 4.0 provide revolutionary advantages. Quantum computing can be used by IoT sensors, robots, and automation systems to improve manufacturing efficiency, supply chain optimization, quality control, and predictive maintenance. Real-time industrial data analysis, anomaly detection, and production process optimization are all possible using quantum algorithms, which also increase productivity and save costs.
Fintech and Financial Services
IoT and quantum computing together have the potential to transform fintech and financial services completely. Quantum-resistant encryption, secure authentication, and fraud detection algorithms can be advantageous for Internet of Things (IoT) devices used in banking, payment systems, and financial transactions. In the financial markets, quantum-enhanced analytics can boost cybersecurity, algorithmic trading, risk assessment, and portfolio optimisation, fostering innovation and giving businesses a competitive edge.
Energy and Utilities Management
In the energy and utilities industry, energy generation, distribution, and consumption may all be optimized with the help of quantum-powered IoT systems. Quantum computing can be used by IoT sensors, smart meters, and grid management systems to provide real-time energy monitoring, demand forecasting, integration of renewable energy sources, and grid resilience. In the energy sector, quantum algorithms have the potential to maximize energy efficiency, lower carbon emissions, and improve sustainability programmes.
Supply Chain and Logistics
The Internet of Things with quantum enhancements provides revolutionary possibilities for transportation, logistics, and supply chain management. Quantum computing can be combined with IoT sensors, RFID tags, and GPS trackers to provide supply chain visibility, real-time inventory management, and route optimisation. In the logistics and transportation industries, quantum algorithms can reduce risks, handle complicated supply chains, and boost operational effectiveness.
These practical uses highlight the wide range of advantages and effects of fusing IoT and quantum computing technology across sectors, fostering innovation, productivity, and competitiveness in the digital age.
Integration Challenges and Considerations
In order for deployment and utilization to be effective, enterprises must address a number of critical integration problems and considerations in the context of quantum computing and the Internet of Things. These difficulties arise from the challenge of incorporating quantum computing capabilities into current IoT infrastructures, and they must be carefully planned for and implemented. The following are some issues and obstacles related to integration:
Hardware Compatibility
Qubit-based systems and quantum processors are examples of specialized hardware needed for quantum computing, and they might not be easily paired with conventional Internet of Things gadgets. Compatibility checks, hardware updates, and maybe rethinking hardware architectures to accommodate quantum operations are necessary for integrating quantum computing technology into Internet of Things devices or networks.
Software Integration
Programming languages and quantum algorithms are very different from traditional computing paradigms. Knowledge of quantum programming languages (such as Qiskit, Cirq) and quantum algorithms is necessary to develop software applications that can take advantage of quantum capabilities for data processing, encryption, and analytics. There are integration issues that must be resolved when integrating quantum software with current cloud platforms, communication protocols, and IoT software stacks.
Data Interoperability
Sensor readings, telemetry data, multimedia material, and real-time streams are just a few of the many types, formats, and protocols that are produced by IoT ecosystems. In order to bridge the gap between quantum data processing and IoT data analytics, data preparation, standardization, and transformation techniques are necessary to ensure data interoperability between quantum-enabled applications and IoT data sources.
Scalability and Performance
For some types of calculations, quantum computing can be more scalable, but it also presents challenges related to hardware resources, quantum error correction, and algorithmic scalability. To ensure effective and scalable operations, integrating quantum computing into large-scale IoT installations necessitates evaluating scalability needs, optimizing resource allocation, and benchmarking performance measures.
Security and Privacy
It is necessary to address security and privacy issues at several levels to integrate quantum-enhanced security measures into Internet of Things infrastructures. Ensuring end-to-end security across quantum-enabled IoT networks and safeguarding sensitive data from quantum attacks require the integration of secure key management, quantum-safe communication protocols, and quantum-resistant encryption into IoT security architectures.
Cost Considerations
Although still in its infancy, quantum computing technologies come with hefty price tags for things like training, maintenance, software development, and hardware procurement. Businesses must assess whether integrating quantum capabilities into Internet of Things deployments is cost-effective, considering budgetary restrictions, ROI, and long-term sustainability.
Regulatory Compliance
When incorporating quantum computing into Internet of Things ecosystems, adherence to industry standards and regulatory requirements is crucial. When implementing quantum-enabled solutions in Internet of Things applications, compliance with data protection rules, encryption standards, and privacy laws may be necessary.
It takes a multidisciplinary strategy, including cooperation between experts in quantum computing, IoT developers, cybersecurity specialists, and regulatory agencies, to address these integration issues and considerations. To guarantee the successful integration of quantum computing capabilities into IoT infrastructures while minimizing potential dangers and optimizing the advantages of quantum-enhanced IoT solutions, organizations should carry out comprehensive assessments, pilot projects, and risk analyses.
The Future is Quantum
The prospects for fusing quantum computing with IoT in the future provide a revolutionary array of opportunities with enormous potential for growth and innovation. IoT systems with quantum enhancements are set to transform industries by facilitating real-time data processing, improved security, and sophisticated analytics capabilities. With the use of these technologies, businesses will be able to optimize operations, make data-driven decisions, and gain fresh perspectives on customer behavior, industry trends, and operational efficiency.
Secure communication protocols and quantum-resistant cryptography are two critical areas of potential that can strengthen IoT networks against cyberattacks using quantum computing. The scalability advantages of quantum computing will solve the scalability issues in Internet of Things installations, allowing for effective workload control and resource allocation. Furthermore, the combination of IoT with quantum computing will promote cooperation, knowledge exchange, and the creation of IoT solutions that are prepared for the quantum age. These developments will drive industry changes and open up new opportunities for competitiveness and growth.
Professionals with experience in quantum computing, IoT architectures, cybersecurity, and data analytics will be in greater demand as businesses adopt quantum-enhanced IoT technology. To fully realise the promise of these revolutionary technologies and equip the workforce for the quantum-powered IoT future, research, education, and training programmes will be essential.
Conclusion
In summary, the nexus between IoT and quantum computing signifies a critical turning point in the development of data processing and digital security. The exceptional computational capacity and sophisticated algorithm handling of quantum computing present hitherto unseen possibilities for improving data analytics, encryption, and decryption in Internet of Things systems. However, new security difficulties do come with these opportunities, especially in the area of quantum-resistant cryptography.
To counter the growing threat of quantum-powered assaults, it is essential to implement cryptographic solutions that are immune to quantum fluctuations. These technologies strengthen IoT networks against potential vulnerabilities by utilizing quantum-safe encryption methods and quantum key distribution protocols. Organizations can strengthen the resilience and integrity of their IoT infrastructures, protecting sensitive data and guaranteeing secure communication channels in the quantum age, by putting in place quantum-resistant cryptographic methods.
Proactive steps, such as investing in quantum-resistant security protocols, encouraging cooperation between IoT and quantum computing businesses, and prioritising cybersecurity education and training, will be crucial as the IoT landscape develops and quantum computing reaches maturity.
Organisations can confidently and resiliently manage the challenges of the quantum-powered Internet of Things ecosystem by adopting quantum-enhanced security policies, staying committed to data protection and integrity, and staying ahead of the curve.